News
Trust and Safety Engineering
I was honored to serve as a judge at Stanford this week for the final projects in CS 152: Trust and Safety Engineering, a pioneering course led by Alex Stamos.
Thirty industry judges supported the work of 120 students, who presented thoughtful systems using large language models to address issues such as sextortion, suicide, investment scams (also known as “pig butchering”), and political misinformation. Students were asked to design holistic solutions that went beyond traditional CS coding assignments. Many interviewed victims, created test cases to identify false positives and false negatives, and mapped out support workflows, including scenarios where strong intervention was necessary.
I was excited to learn that this class is now being taught at several other institutions. Beyond the growing interest in trust and safety, courses like this help shape a generation of engineers who go beyond building just functional computer applications: they are building responsible technology that reflect the human impact behind every line of code.


The End of an Era
It’s a wrap! After 6 years and 8 months, it’s time for new adventures.
Being part of ServiceTitan’s journey from the pre-unicorn days to post-IPO has been nothing short of extraordinary. I feel incredibly lucky to have been trusted to lead such a talented team at a company with a great culture and a mission truly worth fighting for: serving the men and women of the field services trades.
To my team over the years, Paul Intrarakha, Maddalena Scampuddu, Parastoo Sanadi, Nikolai Klyukach, Levon Isajanyan, Naomi Mathena (Walker), Bastian Bartels, Andrew Engelbert, Yuni, Narek Babajanyan, David Babajanyan, Darko Dimitrovski, Siddhesh Rane, Siddharth Chittoor, and everyone else I’ve had the pleasure of working with (you know who you are ;-)) Thank you for your partnership! We built something rare. A security culture so strong that some employees actually said, “I genuinely look forward to InfoSec’s mandatory training every year.” A program built on trust and transparency, one that didn’t just protect customer data but helped them safeguard entire company virtual infrastructures. And last but not least, a program that consistently punched above its weight in the tech world. I truly couldn’t be more proud.
To Ara Mahdessian and Vahe Kuzoyan, you are not only inspiring leaders. You are true role models in caring for the people you serve and family values.
As this ride comes to an end, I feel like a kid who’s just held on tight through a roller coaster strapped to the back of a rocket ship, eyes wide, heart racing, already yelling “again, again!” before it even comes to a complete stop.
Onward! 🚀
CIS
I’m honored to be named one of the Top 100 CISOs (C100) for 2025 by CISOs Connect. This award is especially meaningful because it is decided by a panel of distinguished peers, who understand firsthand the challenges and responsibilities of the role.
The award celebrates the top 100 CISOs in North America, recognizing not only our professional achievements but also our commitment to mentoring and fostering the next generation of cybersecurity leaders. It’s a privilege to be acknowledged by such an esteemed panel of industry peers, and I’m proud to stand alongside this incredible community of forward-thinking security professionals.

ServiceTitan IPO
On 12/12/24, ServiceTitan made a blockbuster entrance into the public market. The stock soared by 42% on its first trading day, closing at $101 and elevating its valuation to nearly $9 billion. For me, this milestone represents the culmination of years of hard work, countless lessons, and a team effort like no other.
Over the course of 6+ years, I’ve had the privilege of leading ServiceTitan’s security program from the ground up, transforming it into a robust, forward-thinking program. We went public with no material weaknesses and became the first company to recognize AI hallucinations as a risk, raising the bar in risk transparency.
A huge thank you and kudos to every Titan and former Titan who contributed to this journey. Special thanks to everyone who was part of the information security team. Regardless of the IPO, I couldn’t be prouder of our accomplishments.

Glendale Tech Week
During the last decades, SoCal’s tech community has become increasingly active, and Glendale Tech is another proof. This month I had the distinct pleasure of being part of a standout panel titled Securing AI: Real-World Strategies for Cybersecurity and Operational Governance. Discussing the future of AI and cybersecurity alongside a great group of panelists was a highlight for me. Gary Askew, my longtime friend Laz, Ravi Singh, and Jensen joined me, and the brilliant Areg Alimian skillfully moderated the conversation.
25 Ways to Make the SOC More Efficient and Avoid Team Burnout
The CISO Series interviewed me and other CISOs on how to make a Security Operations Center (SOC) more efficient. The result is an absolutely jam-packed article with tons of great advice from more than 50+ security professionals.
The next wave of data breaches
If you thought traditional data breaches were worrisome, the next phase in cybercrime takes it to another level. In this article, I explore these evolving threats and suggest practical steps to protect yourself.
Making Security Visible
Many people says that information security is only noticed when an incident happens. In order to create trust with customers, it’s crucial to show them that security is part of everything that that company does. Customers should have easy access to compliance reports that are made to be shared externally. By being open and proactive about your security measures, reassure customers that their data is in safe hands. This transparency builds trust and positions the company as a responsible and reliable partner.
My InfoSec Team Made Our Q2 Planning Meeting Unforgettable

InfoSec had a Q2 planning meeting yesterday, and the team surprised me with this gift. In the small letters, it says, “We are lucky to have you. We really mean IT”.
Security is not an easy job, but I find great satisfaction in working with many teams. A great team with good, fun people is an asset that should never be overlooked.”
CISO LA Panel
I look forward to participating in the CISO Meet LA event at Fogo De Chao, a Brazilian BBQ restaurant that resonates with my Brazilian roots. 🙂
The panel is titled “David & Goliath,” and we will discuss challenges and strategies relevant to CISOs today.
Nobody gets fired for buying IBM
Contrary to the common industry practice of relying on fewer platforms, Bessemer predicts that the continuous evolution of threats necessitates innovative startups to furnish cutting-edge, specialized defenses. This aligns with a principle I’ve supported for years—endorsing the need for specific tools to tackle emerging dangers effectively. I’m honored to be quoted trailblazing this trend.
SINET Silicon Valley
I am honored to join my Executive peers as a speaker at the 17th Annual SINETSilicon Valley Forum on March 21st. I will join moderator Gary Hayslip, Chief Security Officer, SoftBank Investment Advisers on the panel Approaches to Building a Secure GenAI Environment, including Erik Naugle, VP Cyber Security, Intuit, Mike Ratliff, AVP, Security Engineering & Operations, Providence Health, Anmol Misra, Senior Director Infrastructure Security, Autodesk, and Hemanta Swain, CISO Global Head of Security and Compliance, Lucid Motors.
View all speakers, the compelling agenda, and register here.

The Evolving Role of the CISO: Ventures, Leadership, and Societal Contributions
The digital pages of the CISO Connect Magazine recently featured my journey as a Chief Information Security Officer (CISO). This magazine edition included my experiences in venture investing, consulting, and engagements with various vendors.
The magazine is evidence of what I’d like to call the modern CISO mindset. It embodies the essence of a role that has evolved dramatically over the years. It represents individuals who are not just gatekeepers of cybersecurity but are also pioneering strategists comfortable with navigating the complexities of risk in both their professional and personal lives. The images in the magazine of fellow CISOs skydiving, scuba diving, and performing snowboard jumps are not just breathtaking visual content but are powerful metaphors for our daily lives. These are illustrations of our comfort with measuring, managing, and mitigating risks, trusting our skills and preparations to land safely.
Perhaps what resonates most with my philosophy as a CISO is my relationship with vendors. The modern cloud infrastructure, with all its advantages, introduces complexities and challenges that necessitate a symbiotic relationship with vendors. These partnerships are crucial for developing a nuanced understanding of potential vulnerabilities and crafting robust defenses against them. My feature discusses this collaboration, showcasing it as a cornerstone of modern cybersecurity strategy.
Thank you to CISO Connect for this incredible honor, and to all my fellow CISOs, may we continue to jump, dive, and soar to new heights, both in our careers and beyond.
Bringing Transparency to Cybersecurity: Practitioner Stories
I’m genuinely excited about this panel with Lisa Hall, CISO at SafeBase, Lenny Zeltser, CISO at Axonius, and Avani D, CEO at Schellman. We’ll cover topics such as B2B buyer expectations, cross-functional partnerships, and scalable programs for demonstrating trustworthiness to buyers and customers.

Feats of Strength Magazine
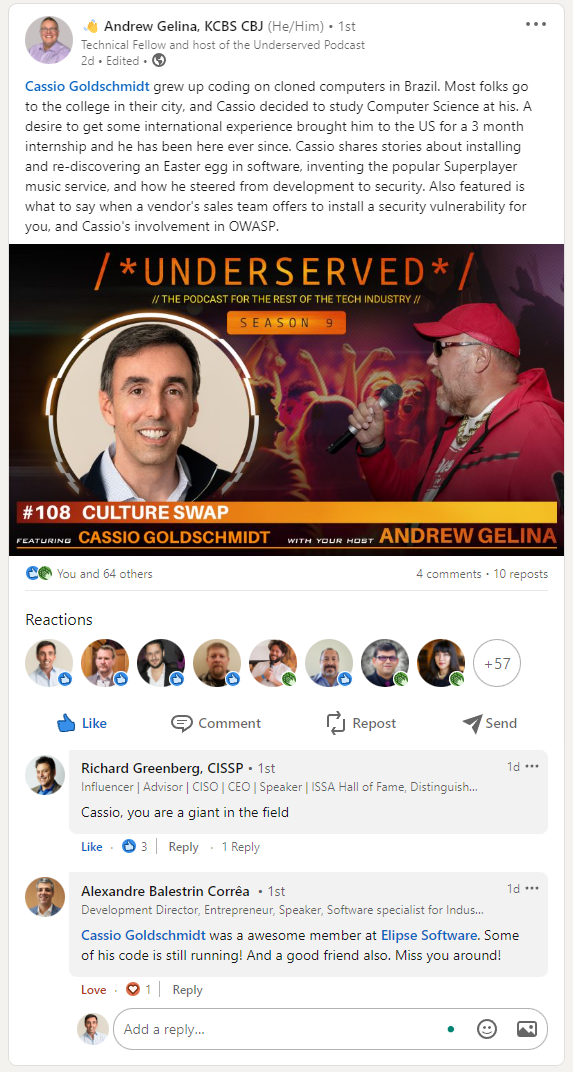
The Underserved Podcast
My interview on the “Underserved” podcast is out. Unlike other podcasts, the interviewer focused on my career and my journey to the USA instead of focusing on technical and managerial issues/
ServiceTitan Pantheon 2023
At ServiceTitan’s customer conference, I co-presented a talk on how we secure the AI solutions we create. The focus was on generative AI and its impact on the trades.
Generative AI is revolutionizing how businesses operate. The talk delivered a comprehensive overview of how we utilize generative AI and data securely to benefit the trades industry. Below are the first 3 minutes of my part of the presentation. The full presentation is available on ServiceTitan’s customer portal.
Back at the beach!
Super excited to return to the beautiful Santa Monica beach for the much-awaited ISSA LA Summit XIII 2023 CISO forum. This year, I am grateful to have the opportunity to facilitate a roundtable discussion concerning the important role of phishing tests in our present technological scenario. See you October 4 at the Annenberg Beach House!
Check out the promotion video below if you are unsure whether you should attend this conference.
OWASP Top 10 LLM is out!
I am excited to see that the OWASP Top 10 for Large Language Models (LLM) taxonomy document has finally been released. This ambitious project brings much-needed clarity to the field of LLM applications, highlighting key vulnerabilities and providing invaluable recommendations for hardening these applications against potential attacks.
Having always been passionate about both developer security and AI for the last 4 years, the OWASP Top 10 for LLM couldn’t be more up my alley. Over 130 specialists, including myself, contributed their insights and knowledge.
Yet, it’s important to note that this breakthrough is only the beginning. LLM technology is an evolving, dynamic field. As technology advances, the security risks and associated adaptations will continuously need to be reassessed and updated.

The 2023 CISOs Connect Top 100 CISOs 2023

I’m ecstatic with the news that I was listed among this year’s CISOs Connect Top 100 CISOs Award recipients, especially in light of the fact that there were over 700 applicants this year! All with at least 5 years of experience as CISOs of sizable companies!
Humbled to be listed among CISOs from companies like Walmart, Bank of America, HP, MasterCard, GE, Jack Henry, Marsh, Blackstone, Target, USAA, Freddie Mac, Unilever, and Fannie Mae.

CISO Series
I had the most excellent time chatting with Rich Rich Stroffoline in today’s Cyber Security Headlines podcast. Here is a summary of some of the topics we covered.
US Military Personnel Receiving Unsolicited Smartwatches
US military personnel have reported receiving smartwatches in the mail unrequested. While it’s theoretically possible these could be used as spying devices, it’s more likely a ‘brushing’ scam meant to drum up fake reviews. If you receive one, it’s best not to turn it on and report the incident.
Chinese State-Backed Hackers Infecting European Hospital
A European hospital was hit by a USB attack linked to Chinese hackers. The incident serves as a reminder that robust endpoint security is vital, showing that even notorious social engineering tricks can be effective without it.
Flight Disruptions from 5G
The upcoming 5G network may disrupt some flights due to overlapping frequencies with aircraft altimeters. Potential measures to deal with this include creating buffer zones and updating aircraft equipment.
Data Breach at Airlines Due to Third-Party Vendors
American and Southwest Airlines suffered data breaches due to a hack on a third-party vendor. The incident highlights the importance of ensuring your third-party vendors adhere to the same security standards as your company and having a response plan for breaches.
Potential US Export Bans on AI Chips
The US is considering significant export bans on AI chips, a move reminiscent of past restrictions. While it may help the US maintain its technological edge in the short run, it might also incentivize foreign competitors to develop their own technology.
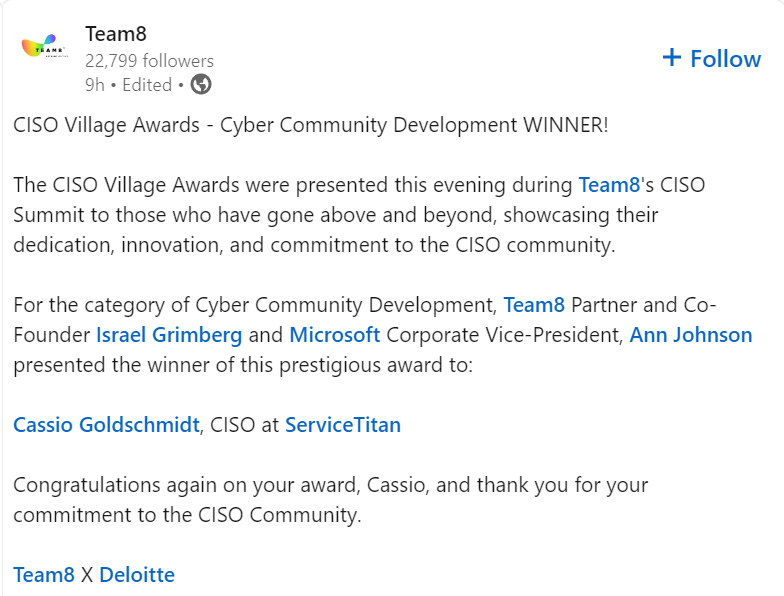
Team8 CISO Summit Awards
Honored and humbled to be recognized in Tel Aviv by Team8 and Deloitte with the Cyber Community Development Award. Team8 has been a longtime supporter of the CISO community, promotes high-quality security papers, and assists in establishing some of the world’s most innovative security firms.


ServiceTitan Pantheon 2023
Excited to announce that I will be presenting at the ServiceTitan Pantheon once again! This year’s session is all about “The Future of GenAI and ServiceTitan”. Together with Sarah Sheehan, Group Product Manager at ServiceTitan, we’ll explore how Generative AI can solve many current challenges and discuss the opportunities it presents for ServiceTitan customers.
Generative AI and ChatGPT Enterprise Risks
Excited to share our paper on generative AI and ChatGPT security, which I had the pleasure of co-authoring with a fantastic global team under the leadership of Team8 Gadi Evron.
I am a strong proponent of #GenerativeAI and I am pleased that we were able to debunk some myths, provide guidance, and consider the risks associated with this cutting-edge technology. This paper is a good starting point for security practitioners who are being requested for guidance by their organizations and still need to catch up with the technology.
Download our full CISO guide on Generative AI here.

Battery’s Cyber Readiness Webinar
Looking forward to the upcoming Battery Ventures cyber readiness webinar alongside Daniel Schwalbe, CISO of DomainTools, open for all Battery Venture invested companies. In this by-invitation-only webinar, we will be discussing strategies for building a strong cybersecurity posture for organizations at any stage of their security journey.

Taking care of your people
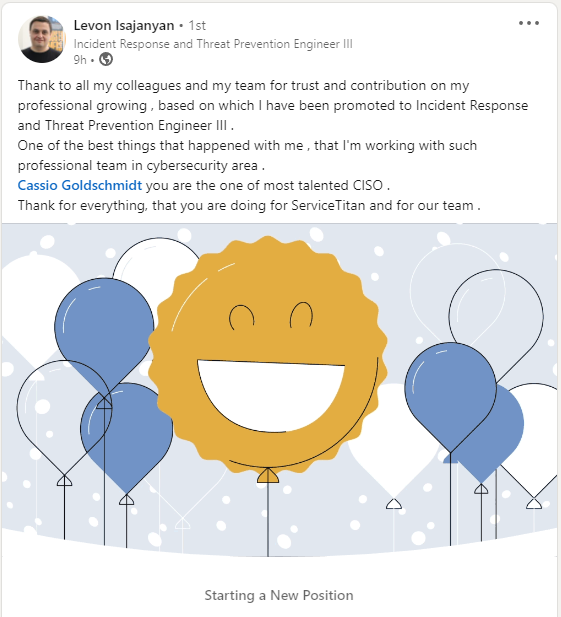
One of the greatest joys of leading a team is providing the opportunity for the team members to grow and achieve self-realization in their professional lives.
Collaborating with colleagues you respect and admire at work is the employment equivalent of finding a golden ticket in your chocolate bar – it’s a rare treat that makes the daily grind infinitely more enjoyable.
During Levon’s employment interview, I asked him how he maintained his expertise as an incident response professional. I anticipated an answer related to reading books and the news, given that he was not yet employed full-time in his field of work. Instead, he went beyond stating that he did volunteer work to defend journalists from hacker groups. I knew instantly that Levon possessed the hunger I was seeking in a team member.
Congratulations on another well-deserved promotion, Levon. I am certain that this will not be the end.
SafeBase Customer Advisory Board
SafeBase’s first Customer Advisory Board meeting was a resounding success, thanks to the SafeBase team’s meticulous preparation of a clear session agenda and topics. Representatives from companies such as LinkedIn, Crossbeam, ServiceTitan, Abnormal Security, Jamf, Axonius, Confluent, Split, and Sigma attended the meeting in Scottsdale, Arizona.
One of the most exciting topics we discussed was the industry trend of creating a Chief Trust Officer position. Jim Alkove’s fireside chat was especially enlightening, as he discussed the shifting role of security to a trust leader. This topic was timely and relevant, given the increasing importance of trust in today’s digital landscape.
Check out the SafeBase blog post on the topic. The tips and takeaways shared by the SafeBase team are useful and applicable to anyone hoping to hold a similar event with their advisory board or stakeholders.

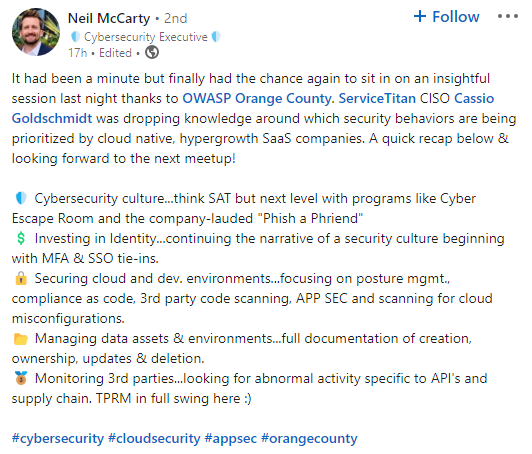
Thank you, OWASP Orange County
What a joy to go to OWASP Orange County to present my talk, “Security for Growth Companies.”!
The turnout was amazing: the room was packed. People asked great questions, and it was exciting to see the audience’s engagement. It was also great to catch up with old friends, many of whom I hadn’t seen in a while.
What’s even more exciting is to see the next day that people found value in the talk and the way we run our security program!
Future of Cyber Risk
Recently, I had the pleasure of being interviewed for the Future of Cyber Risk Podcast. During the episode, we discussed my role as Chief Information Security Officer at ServiceTitan, a vertical SaaS B2B company. David asked me to share what a day in the life of a CISO looks like, and I explained that security must come before compliance, but, in the end, business success should be the priority. I also shared my views on cyber risk management.
TEN ISE West Award 2022
Tonight, I was once again honored to accept another set of awards on my team’s behalf. The team’s work on ServiceTitan’s Smart Trust Center (https://security.servicetitan.com) earned us a spot among the three finalists for the best project award at the 2022 TEN ISE West. The project attests to our commitment to innovation, excellence, and transparency in information security. After ServiceTitan established this portal, many of the “cool kids” many of us look to for direction, such as InstantCart, DataDog, LinkedIn, JAMF, SNYK, Postman, and Discord, jumped on the boat we took with a pre-Series A company to establish their portals using the same technology. Companies such as Blackstone, Lilly, and AT&T were competing against us. They all have a market cap that is more than ten times that of ServiceTitan and a disproportionately larger amount of resources in InfoSec.
I would also like to express my gratitude to the distinguished group of judges for nominating me for an executive award.


The CISO Experience
On Wednesday, November 23, at 12 p.m. EST, I will have a live conversation with the fascinating innovator and forward-thinking Simon L. I can hardly wait!
The most gratifying reward
The greatest reward is helping a stranger on the other side of the world who you will probably never meet. Below is a LinkedIn post someone did this week about my LinkedIn Learning course.

ISE T.E.N. West Award Nominees 2022
I am honored to be among the nominees for the ISE West Executive Award. Team ServiceTitan was also put forward for the ISE West Project of the Year Award by a group of very qualified experts and industry professionals, which makes me very humble. Thank you, T.E.N., for your consideration and for consistently hosting a phenomenal event.
Segregation of Duties
This may sound very strange, but after approximately 13 years of involvement with the OWASP LA chapter, I’ll be presenting a talk for the first time. The reason is simple: for the longest time I was at large the person in charge of selecting talks and I never felt comfortable selecting my own talks. I’m very thankful that the board reached out to me for this in person talk. I’m super excited with this special opportunity.

C|VISION – CXO Think Tank
I’ll be a featured speaker at C|VISION CXO Thinktank in San Francisco on September 14, 2022. Steve Zalewski, Jared Snowm Sammuel Washington, Leda Muller, Rick Bosworth, and I will be addressing attacks on the supply chain.

Security for growth companies
Cloud has transformed the nature of the technology used to build systems. It also expanded the attack surface.
In this post, our group CISOs shares 5 Security principles to help founders, builders, and security practitioners respond to emerging and novel digital threats.
Congrats to all CISOs who made the CISOs Top 100 CISO (C100) 2022 in North America
The C100 list was released today and I must say that it took days to review and verify references for several hundred candidates. Here are a few reasons why I consider the C100 award special:
- Experienced CISOs review and select the winners
- All candidates must have at least five years of experience as a CISO or equivalent position
- We consider the candidates’ involvement and leadership roles in professional organizations
- Volunteering and activism are part of the selection criteria
- Last but not least, the board considers mentoring, teaching, and educating future cybersecurity professionals across business and technical functions
The criteria are super transparent, and there is no fee or financial requirement at any point associated with the C100 awards.
To all winners of the C100 2022, I salute you!

By invitation only Glilot CISO event
Congrats to Glilot for organizing a great event for their CISO advisors and startup leaders during RSA. There were some great discussions with the group. Time well spent!

Let’s talk Dev!
If you are attending RSA, come join Emilio and I on this panel about Dev environments on June 7, 2:30 PM at the Mourad! Emilio is a very experienced practitioner and I look forward to talking to him about this vital topic for any company developing SaaS products.

Israel Cyber Event
Looking forward to watch the investor panel and serve in the CISO panel at the Israel Cyber Event organized by the California Israel Chamber of Commerce (CICC) on June 8th! FREE registration in this link: https://lnkd.in/gzZUN6Jc

ServiceTitan Pantheon 2022
Pantheon 2022 was an absolute success. This year the conference took place at the historic Los Angeles Coliseum. Tom Howard and Sendur Sellakumar did a superb job describing the company’s vision to propel the industry forward with technology. During this presentation, they provided some of the concrete findings the company made from mining data.
Although I wasn’t present at the conference (because I was on vacation in Mexico with my family), I was humbled by Tom Howard’s off script shout-out to InfoSec and specifically to my work around 23:45 in the video below.
ServiceTitan Launches Cybersecurity Hub
It was a pleasant surprise to see my employer’s announcement about our Smart Trust Center today on LinkedIn. ServiceTitan’s “self-serve” access allows customers to gather information about the company’s security program quickly. This includes audit reports, security certifications, results from automated scores tools, whitepapers, security policies, and a plethora of information grouped into tiles.
2022 CISOs Top 100 CISO (C100)
I’m honored to join this community and serve on the 2022 CISOs Top 100 CISO (C100) Board of Judges. I appreciate the opportunity to work with this esteemed group of experienced CISOs and be part of an award with transparent criteria and is not shy to show the faces of the board of judges.

A Virada Talks: A very special podcast
With so many outstanding podcasts out there, I feel biased to call “A Virada” my favorite Brazilian Podcast. A Virada is a podcast about innovation and the future of markets and it’s a true forward thinking podcast. In 2021, A Virada made the top of iTunes list in the business category, passing internationally acclaimed podcasts such as the Harvard Business Review (HBR). Above all, the two hosts are what make this podcast so special to me: the head of Prana Venture Capital Bruno Peroni and the co-founder of Superplayer & Co, Gustavo Goldschmidt, my younger brother.
In this episode in Portuguese of A Virada we talked about Information Security, the current threat landscape, privacy, Internet of things (IoT), and much more.

8,000 learners and counting on the first 5 months
In only 5 months, “Practical Privacy for Products and Services” surpassed the 8,000 learners mark. Publicly listed companies around the world are starting to make this course mandatory for their employees.
#privacybydesign

Detection at Scale Podcast
In this episode of Detection at Scale, Matt Naglieri and I chat about the importance of bringing the right people to join a team, regardless of company size. I also provided some of my thoughts about outsourcing, decision-making, and future demands for security teams. Check it out!

Practical Privacy For Products And Services
Course Description
One of the biggest threats to your personal information is a lack of cybersecurity. The same rings true for organizations that need to protect their data. This course offers you a strong understanding of what you can do as an individual contributor to help keep your organization’s data safe. In this course, Cassio goes over processes for identifying data that needs to be protected, as well as classifying and sorting data most effectively. He explains data processing, including how to address some common mistakes and remove processing bias. Cassio provides a detailed look into privacy policies, training, and breaches, as well as sharing proven strategies to manage privacy risks.
CISOs Top 100 CISOs (C100)
I’m feeling ecstatic to receive the CISOs Top 100 CISOs award from CISO CONNECT! This recognition is truly a collective win with the help of my amazing team and executive leadership that supports our initiatives day in and day out! Without this collaborative effort, we wouldn’t be where we are.
A heartfelt shoutout to my incredible colleagues and former board members at OWASP LA and the OWASP Foundation for working tirelessly with me to give back to the security community outstanding educational opportunities and the AppSec California conference, which many consider one of the best Application security conferences in the world! I cannot thank you all enough for your support!
– Announcement: https://lnkd.in/gaKUQVW
– C100 Winners: https://lnkd.in/gMVJD6E

The Cyber5 Podcast
I had a great time chatting with Landon Winkelvoss in the Cyber5 podcast.

SE Day 2021 – 3rd Edition
I’m thrilled with my alma mater’s invitation to be the keynote speaker of this year’s SE Day event. By choosing a keynote on application security for a software engineering conference, PUC-RS sends a strong message to its students that security and privacy are indeed paramount.

Passed My Certified Bitcoin Professional Exam… Again
For the last 7 years, I’ve been a certified bitcoin professional. Because of the continuous enhancements in the field, this certification expires every two years. This is the 4th year I take the test.
A Certified Bitcoin Professional is knowledgeable about the Bitcoin blockchain, Bitcoin transactions, and how the Bitcoin network operates. CBPs are able to apply Bitcoin technology to their professional area of expertise and understand privacy aspects, double-spending, and other issues that relate to the currency.

Something Really Cool Is In The Works…
Just wrapped my latest course Madecraft! Looking forward to sharing the finished product soon!

Addressing The Security Challenges Of Shadow IT With Cassio Goldschmidt, CISO At ServiceTitan
I had a great time with Amir Bormand, Managing Director at Elevano, chatting about the risks of unapproved IT services to an organization in The Tech Trek podcast part 1 and part 2.

ServiceTitan Wins At The ISE® West Digital Awards Show
ServiceTitan won the ISE┬« West Executive Forum and Awards 2020 in the “project” category, debunking a little company called T-Mobile that you may have heard about.
Winners and nominees in other regions include equally small companies such as Aflac, Cox, Southwest, Mastercard, ADP, and others.
Pantheon 2020
Pantheon will be an online conference this year and ServiceTitan is maintaining its high standards of quality. The company shipped 5 large boxes of professional video equipment to my home to practice and record material for the conference. Can’t wait to see the result.
A Virada Podcast – The Future Of Coding
It was a very special honor to be a guest at A Virada Podcast for two reasons.
- One of the two hosts is my brother, Gustavo Goldschmidt.
- A Virada is the #1 podcast in Apple’s overall rank in Brazil

A Talk About Privacy And Brazil’s LGPD
BrazilΓÇÖs General Data Protection Law has officially come into effect. The new law has a lot of similarities with GDPR and CCPA/CPRA, however, LGPDΓÇÖs applicability is NOT limited only to businesses and organizations above a particular size but applicable to businesses of all sizes, with the exception of journalistic, artistic, and academic purposes, or public safety and national defense.
Every company that processes data in Brazil or sells services to Brazilian consumers needs to comply. In this talk with Julio Lanes, Partner at Andrade Maia Law Firm, Julio and I chatted a bit of my personal experience with the impact of privacy laws in the US and how companies reacted to it.
Agent On Influence Podcast
I had a great conversation with AppSec thought leader Nabil Hannan on the NetSPI’s Agent Of Influence podcast. During our talk, we covered a broad range of topics, industries, and application profiles.
Some highlights of our conversation include:
- Does one size fits all in AppSec?
- How do you create a safe environment to promote open test of highly sensitive systems?
- Are open-source solutions more secure?
- The fundamental difference between security software and software security

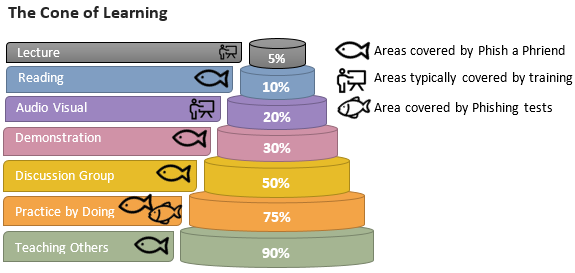
Phish A Phriend
The COVID-19 situation opens up new work from home risks and cybercriminals are taking advantage of it. One of the ways companies can prepare employees is to send out simulated phishing tests. In my article Improve Your Company’s Resilience Against Phishing Attacks By Inviting Employees To Phish I describe Phish a Phriend, a more engaging, effective, and fun way for enterprises to roll out their phishing tests.
ServiceTitan Founders Club 2020
I feel truly honored for being selected as one of the 87 extraordinary employees who was selected to go to Cabo. Founders’ Club is the highest honor awarded at ServiceTitan and recognizes you as one of the top performers in a company full of star performers.

T.E.N Information Security Executive North America Awards 2019
Honored to be one of the nominees for the T.E.N Information Security Executive (ISE) Award North America 2019. T.E.N. is a technology and information security executive networking and relationship marketing firm. The award is given to top-ranking decision makers representing organizations in the academic and public sectors, commercial, financial services and health care.

(ISC)2 Information Security Leadership Americas Awards 2019
I am this year’s winner of the (ISC)2 Information Security Leadership Americas and I feel deeply honored to be selected by a program created by an organization with over 140,000 members that recognizes outstanding leadership and achievements in workforce improvement of information security and management professionals throughout the private and public sectors in North, Central, and South America.
Armenia, Here I Come!
I’m traveling to Yerevan in Armenia for the first time next week and I’m really looking forward to all the upcoming events, including the opportunity to meet the OWASP Armenia community, give a talk at the American University of Armenia, attend the Hive Ventures Summit, attend the WCIT, meeting the staff and ServiceTitan, and hire our first information security team member overseas.

Yerevan , Armenia: Cascade Complex monument landmark of Yerevan capital city of Armenia
Interns At ServiceTitan
Providing growth opportunities for my team members is paramount. When HR asked all ServiceTitan interns who wanted to be featured on a LinkedIn post about the 2019 internship experience, Sid was the first person companywide to volunteer. Sid had many internship options and I’m glad he chose to join the team.

FACIN Is Now 40 Years Old!
Happy 40th birthday, FACIN school of Computer Science at PUC-RS! Thankful for all I learned from you. I am honored to be part of your history and humbled to be one of the 6 selected alumni case studies (in all 40 years) featured in the 40th-anniversary commemorative book.

Entrepreneurship Podcast
In this podcast in Portuguese, Eduardo and I talked about the importance of information security in the development and growth of startups and companies. We touched on case studies and I gave tips on how companies can start protecting their data.

Cybersecurity At The Board Level

Leaders have a significant responsibility in personally understanding and managing cybersecurity as a key risk area. They must learn how to proactively protect their organizations and customers from the ever-increasing threat of cyberattacks. I felt honored and humbled when a chapter in Brazil of the Young Presidents Organization (YPO), a global network of young chief executives with approximately 24,000 members in more than 130 countries, invited me to fly all the way to South America to speak on the topic of roles and responsibilities to their local group of business leaders.
M&E And Secure Content Creation
The Media and Entertainment (M&E) industry has many “crown jewels” that require protection from hackers and malicious insiders. These jewels include intellectual property like video content and concept art, business data like highly sensitive email conversations, and personnel records. They also include the availability of content streams to ensure consistent, accurate delivery of media assets. It’s an area where digital security, innovation, conversion, and file content management is converging to redefine the daily experiences of M&E businesses.
This month I passed the strict review and approval process to become a qualified Trusted Partner Network (TPN) assessor. The TPN is a joint venture between two major entertainment industry associations, the Motion Picture Association (MPA) and the Content Delivery & Security Association (CDSA), the worldwide leaders in third-party entertainment industry assessments.

Reducing Cyber Exposure From Cloud To Containers Mighty Guide
Securing the modern attack surface is a critical challenge you must effectively address to reduce cyber exposure and protect your enterprise. The Mighty guide Reducing Cyber Exposure from Cloud to Containers provides insights and lessons from 29 industry leaders (e.g., @daveshackleford, @csima, @lady_nerd, @planetlevel, @weldpond) on this topic.

OWASP AppSec Cali 2018 – THE BEST EVER!!!
Great weather, great speakers, greater trainers, great organization = sold out and awesome! Hollywood quality recordings of the talk are coming out soon.
Goodbye #LA and @AppSecCali it was a blast. Probably the best appsec event in the USA. @RAGreenberg @CassioGold
— Eoin K (@EoinKeary) February 1, 2018
Nice to catch up with you again. Not forgetting @manicode – old friends again. pic.twitter.com/YnVucvA4Yr
Great hanging out @AppSecCali with the founder of OWASP Los Angeles! https://t.co/TrVsBn1VzK
— Richard Greenberg (@RAGreenberg) February 2, 2018
Security Test Of The 2018 Presidential Elections Voting Machines: Experience And Results
Brazil’s Superior Electoral Court (TSE) selected me to test the electronic voting machines that will be used in the 2018 presidential elections. In this interview (in Portuguese) conducted by the TSE, all security researchers who provided relevant findings described their work and explained why the test is important.

Forbes Technology Council
Feeling grateful for being hand-selected to become part of the Forbes Technology Council and having the opportunity to submit thought leadership articles on industry-related topics for publishing on Forbes.com.

Penetration Test Of Brazil’s Electronic Voting System
The Brazilian government selected me as one of the security researchers who will test the nation’s electronic voting system. I’m honor and excited about the opportunity to contribute to the security of this critical infrastructure component.
Bug Bounty Panel At AppSec USA 2017
This year at AppSec USA 2017 I be discussed bug bounty with a great team of panelists from companies such as GDS, PayPal, ITSP Magazine, and Baker McKenzie. Here is the video in case you missed it.
Bitcoin Hardfork
On August 1st Bitcoin was split into Bitcoin (BTC) and the clone coin Bitcoin Cash (BCH). The means of this split was both a source code ΓÇ£hard fork,ΓÇ¥ creating an incompatible and independent cryptocurrency, in conjunction with a clone of the entire blockchain. Everyone who had bitcoins (BTC) before the fork has the same number of coins in bitcoin cash (BCH). In an article for the ITSP magazine, I explained the security and risks related to this split by discussing the motives, technical differences, and the consequences to the ecosystem.
Read the full article: Bitcoin’s Fork And Its Security Implications (two-part article)
Innovate Pasadena Cyber Security
According to ITSP TV, the panel at ADP was extremely informative. Check out the video:
ITSP Magazine
Honored to be listed as an Expert on ITSPmagazine.
My first blog contribution is the article: Dodging SHA-1’s Collision Course

17th Annual Cyber Security Symposium
UNC Charlotte 17th annual Cyber Security Symposium was a sold out event. Humbled with the opportunity to take the main stage. Although this is an academia event, there were more far more professionals than students. Kudos to the organization for a great event!

Dissecting Bitcoin Security At RSA
So grateful for the strong attendance of over 600 people at my talk about Bitcoin. As of today, one Bitcoin is worth US$400. How far will it go?

OWASP Top 10 Proactive Controls 2016
Happy New year! OWASP Top 10 Proactive Controls 2016 is out. I’m one of the reviewers. Enjoy!

RSA 2016
Super excited about my upcoming talk at RSA 2016! With 33,000 attendants RSA is one of the biggest, best known, and most respected security events of the year. Here is a picture of a general session.

(ISC)2 Congress
(ISC)2 congress was a massive success with over 20,000 attendants. Happy to be able to contribute to the show as a speaker. Below is a picture of Monday’s lunch. I always wonder how the kitchen is able to serve everyone at the same time. One day I’ll ask for a tour of the kitchen… It will make me a better man (and a better cook).

OWASP AppSec California 2015 Videos Are Out!
Working with Jim Manico is a joy! I hope we can present again soon.
OWASP AppSec California 2015 Rocks!
Following the huge success of the previous event, OWASP AppSec California is promising to be one of the hottest conferences in 2015. The lineup of keynotes and speakers is top-notch and the venue is truly unique. Seating is limited so you really need to hurry up to get in!

FS-ISAC, Here I Come!
Reviewing my talk for next week. Really excited about contributing and collaborating with FS-ISAC on critical security threats facing the global financial services sector.

CIO Event North America
The CIO series which currently operates in Europe, the Middle East, Africa, and many cities in North America is coming to Los Angeles. The event’s mission is to create a world-class platform of end-user-driven academia to help executives make the right decisions for their organizations. I’ll be speaking at the Los Angeles event along with the Coca-Cola CIO, E&Y CTOΓÇï, Carefusion CIO, and LA Unified School District CIO.
Black Hat Brazil – Part II
Wow! The organization committee highlighted my talk as one of the exciting conference briefings! The pressure is on! Better to brush up on my Portuguese for next week!

OWASP LA Rules!!!
I am thrilled to share this one: my excellent friends Tin Zaw, Richard Greenberg, Edward Bonver, Stuart Schwartz, and Kelly FitzGerald were voted the best OWASP chapter leaders in the world and will receive the WASPY Awards during the Global OWASP AppSec USA 2013! Great job people!
Speaking of OWASP AppSec USA 2013, let me take a moment to plug this excellent conference and the impressive lineup of speakers. If you have never been to a Global AppSec (USA, Europe, Latin America, or Asia) before, I highly recommend checking it out!
Black Hat Brazil
The Black Hat Briefings are a series of highly technical information security conferences that bring together some of the most prestigious names from the full spectrum of security thinkers. The conference organization does a superb job staying on the leading edge of new security trends as they emerge.
I was thrilled with the announcement of the first Black hat briefing in Brazil and even more thrilled when I was selected as one of the speakers! Brazil has long been reputed as the king of the banking Trojan. The few hackers who have been arrested are those who have committed such a huge scale of cybercrime that it was possible to arrest them under existing laws such as larceny and conspiracy. The local information security industry needs events such as BlackHat to learn and fight the ever-increasing number of new attack methods in cyberspace.

Hot Topics In Security

Wow! My roundtable session “Hot Topics in Security” at the Digital Insight Innovation Conference is indeed a hot session! Only a few days after the conference registration opened, the session reached maximum capacity. The organizers scheduled a second session on Tuesday for all of you who could not sign up for the first one.
Free Online Training
SAFECode released some training material last week. Some of the main contributors are members of my former staff at Symantec.
If you are looking for this type of material, also consider Jerry HoffΓÇÖs excellent OWASP AppSec Tutorial Series
Lastly, my good friend Zully released a number of good videos about bitcoin security at Khan Academy.
Another Pleasant Surprise!
This year OWASP initiated the first annual Web Application Security Person of the Year (WASPY) award and I’m truly honored to be among the finalists.
Kate Hartmann, one of the few OWASP full-time employees, once told me that babies are the number one project killer in the community, something I can now testify aboutΓǪ As sad as this statement may sound for a security practitioner, I believe this is the ultimate proof that the organization is indeed moved by passion. People dedicate countless hours and really love what they do. If you don’t believe my words, listen to Ivan Ristic’s interview in the OWASP podcast when he talks about OWASP!
I really cannot count how many individuals I met and I have come to admire and built a friendship with. OWASP not only made me a better professional but also a better person.
I’m sincerely touched by this nomination. Thanks, OWASP! See you in Austin!
Global OWASP AppSec LatAm 2011 Videos Are Out
Global OWASP AppSec LatAm 2011 videos are now available on YouTube! I had the pleasure of acting as the host from beginning to end. Here are some of my favorite presentations:
In English:
- Bryan Sullivan – You Are Not Amy Winehouse: A New Plan for Reaching the Developer Community
- Michael Craigue – Security Development Lifecycle – A History in 3 Acts
- Chris Evans – Dosh4vulns — Google’s vulnerability reward programs
- Rob Rachwald – How Security Researchers Are Hurting the Business of Hacking
- Dinis Cruz – Making Security Invisible by Becoming the Developer’s Best Friends
- Maximiliano Soler Mantra – The Security Framework Slides
In Portuguese:
- Alexandre Braga – Como n├úo escolher a sua senha! Ser├í a senha gr├ífica o futuro das senhas?
- Rodrigo Montoro – HTTP Header Hunter: Looking for malicious behavior into your http header traffic
- Magno Logan – Seguran├ºa em Sites de Compras Coletivas: Economizando dor de cabe├ºa!
- Wagner Elias – Automatizando an├ílise passiva de aplica├º├╡es web
The Great Cypher, Mightier Than The Sword
David Ladd (Principal Security Program Manager, Microsoft Corporation), Gary McGraw (Chief Technology Officer, Cigital, Inc.) Kyle Randolph (Senior Manager, Security & Privacy, Adobe) and I will be serving at a RSA Panel titled “Making Sense of Software Security Advice: Best vs. Practiced Practices“. Reeny Sondhi (Director, Product Security, EMC Corporation) will be the moderator.
Join me from February 27- March 2 in San Francisco for five days of learning, sharing and networking. IΓÇÖve seen the agenda and the week promises to be a busy one! As a selected speaker for 2012, IΓÇÖm pleased to be able to extend a discount of $200 off the current registration rate when you use my personal discount registration code. Simply enter the following code when you register online:
My personal discount registration code: ZSPDdJaIoqK
This offer cannot be combined with any other discounts and is valid for new registrations from December 6, 2011 through January 27, 2012. The code cannot be used retroactively. To find out more about RSA Conference and the packed agenda, visit: https://www.rsaconference.com/events/2012/usa/index.htm. Be sure to register using the discount registration code above to receive the $200 savings.

The Right Tool For The Right Job (SAFECode And BSIMM)
After listening to a number of talks at different conferences around the world, IΓÇÖm convinced that even experts are confused about the various security initiatives, particularly SAFECode and BSIMM. As a consequence, organizations are confusing prevalent practices with effective ones. Some of the results of this misunderstanding are organizations trying to choose the most popular BSIMM practices and use them as criteria for suppliers or adopting BSIMM as a Secure Development Lifecycle framework.
This week SAFECode released ΓÇ£A SAFECode Perspective on Leveraging Descriptive Software Security InitiativesΓÇ£. This brief paper addresses common questions on the differences between BSIMMΓÇÖs descriptive model and SAFECodeΓÇÖs prescriptive guidance. If you are responsible for a large software security initiative, I highly recommend reading this paper.
The Gold Standard
Software Development has changed considerably from a decade or two ago. While writing secure code (secure programming) is still a critical component of the secure software lifecycle, there is a great deal more to consider. Formal and structured software development methodology became a necessity for any organization that develops code.
Despite its known flaws, certifications are a great way to attest outsourced development can build solutions with the same level of quality practiced in large and well-established enterprises. Certifications are a good way to verify a certain level of expertise has been reached among team members and to provide a meaningful measurement to customers. Engineers, especially in developing countries, should ponder the recognition a credible certification can bring to their work. I recently provided a quote to (ISC)2 about the value of CSSLP. The certification has reached the 1,000 certified professionals milestone this year and I wonder if it will eventually replace CISSP, known by many as the industry gold standard.
Speaking of (ISC)2, Caleb Sima, Tony UcedaVelez, Mikhael Felker, Stuart Schwartz and I will be speaking at the (ISC)² SecureSDLC 2011 – SoCal November 1st in Anaheim, CA. This should be a great one-day event.
OWASP AppSec LatAm 2011
It took more than a year to organize OWASP AppSec LatAm 2011 but the results were worth the effort. Equipped with numerous auditoriums that can accommodate up to 800 participants, PUC-RS provides a world-class infrastructure. The variety and quality of PUC-RS’s main restaurant are comparable to some Buffets in Las Vegas. In addition, many professors supported the event and were actively engaged in conversations on how to include application security education in the curriculum.
Bryan Sullivan and Michael Craigue, our two keynotes, delivered more than security knowledge in their presentations, they delivered wisdom. Bryan delivered a polished presentation that mixed big picture concepts with hard-core technical demos. Bryan’s unique mixture of skills makes his presentations interesting to all sorts of audiences. Michael Craigue’s conversational style and candidness made his presentation a must-see for everyone who wants to jump-start a security initiative at an enterprise. I highly recommend both.
The local organization worked incredibly hard to deliver a solid conference and great entertainment! Kudos to Alexandre Balestrin Correa (aka ABC), Jerônimo Zucco, L. Gustavo C. Barbato, Lucas C. Ferreira, Rafael Dreher, Gustavo Simon, Leonardo Goldim, Luiz Gava, Sarah Baso, Carolina Nogueira, Mauricio Pegoraro, Luciano Madeira, Adriene Barbato, Maximiliano Soler, Luis Otavio (aka LOD) and Ricardo Makino for a well done job! Argentina now has big shoes to fit for OWASP AppSec LatAm 2012!

A Pleasant Surprise!

(ISC)² Americas Information Security Leadership Awards 2011 took place yesterday. To my complete surprise, I received a special recognition award for community services! Wow, have you ever had the feeling you realized something about yourself just because someone told you?
There is nothing more enjoyable in life than being surrounded by highly motivated and passionate individuals. Performing community services is fulfilling and important: we all know there is a lot to do in application security and I believe we, the practitioners, have a social responsibility to help our communities.
Unfortunately, sometimes I see people leaving not-for-profit organizations because their bosses actively discourage this type of “distraction”. My personal experience as a manager and a practitioner is that these community services and work for an enterprise are symbiotic. In fact, all my staff at Symantec is encouraged to engage in this type of activity. This is a great way to retain, train and acquire talented employees. It’s good for the individual, the business, and the community. I hope other companies start to see things this way.